Depending on the size and complexity of your organization, managing technology can easily become a full-time job. If you are only calling a technician when you are dealing with a computer issue, then you might be sitting on a ticking time bomb. Whether you have internal staff responsible for managing your IT, or you rely on a third-party, you’ll want to make sure the following tasks are getting done.
GTIN Managed IT Blog
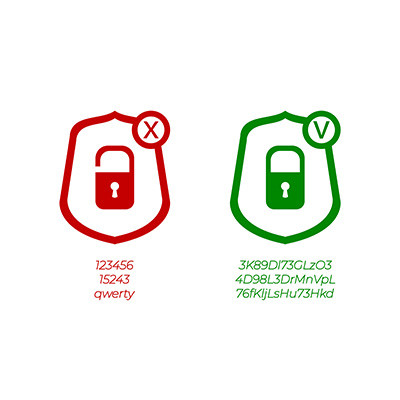
Simple passwords are just not an effective security practice, so if you’re still using credentials like Password, 123456, Guest, or Qwerty, listen up. You need better password hygiene practices before you suffer from a data breach. Here are some ways you can make a better password to protect your business from threats.
Phishing is a remarkably dangerous tactic used by hackers to take advantage of those who might not be quite as in-the-know about security practices. Phishing attacks can be carried out against both businesses and individuals alike, and due to the many different forms these attacks can take—including email, text message, and even fraudulent websites—they can be quite problematic.
Phishing is a common issue that businesses of all kinds can experience, whether they are a small startup or a large corporation. Hackers are always trying to extol information from your employees, including account credentials, remote access to your systems, and in some cases, funds directly from a bank account. It’s up to you to teach them how to identify and respond to phishing attacks.
Password changes, multi-factor authentication, and countless changes in policy and procedure can make daily workflows more and more complicated. Cybersecurity can truly be a pain—a necessary pain, granted—but a pain nevertheless, and one that can gradually lead to burnout if you aren’t careful. Let’s go over how to mitigate the likelihood of it.
Do you have an old Google account that you created years ago, only to replace it later with one that is more on-brand and less filled with spam messages? You’re not alone, but as you might expect, these accounts can create more problems than they are worth if you let them sit around unused for too long. Perhaps that is why Google is planning to shut down any old Google accounts that have remained dormant for the past two years.
For the small business, technology is an issue; and reasonably so. For something that holds so much importance for an organization, there are bound to be problems attached. These problems can disrupt efficient workflows and ruin some situations. In this week’s blog, we will take a look at four things you can do to cut down on your technology troubles.
In today’s business, sharing files is easy and something many workers take for granted. Unfortunately, not all file-sharing methods are secure. When efficiency is prioritized over security, it can often lead to extremely troublesome situations. For this week’s tip, we thought we’d go through a half dozen practices you can take to ensure your files get to where you need them to get safely and securely.
If you watch technology news, you might notice that there is one day out of every month that gets a lot of attention from the technology sector, and that day is what is called Patch Tuesday. This is the day each month when Microsoft issues all of their patches and security updates, and it’s important to know when this day falls each month—at least, for your IT team it is.
At first glance, cybersecurity might seem incredibly complicated and difficult to understand, but even a baseline understanding of some of the principles of cybersecurity can go a long way toward protecting your business. Let’s discuss some of the common-sense ways you can keep your business secure, even if you don’t have an internal IT department to ask for help from.
Regular computer maintenance is part of maintaining healthy IT infrastructure, but one aspect that can often go by the wayside is keeping your computer physically clean. By this, we mean keeping it dust-free, clean and tidy. We’ve put together a shortlist of everyday actions that employees of any caliber can use to keep their workstations clean. This will help your organization take preventative measures over time and (hopefully) prolong the lifespan of your business’ technology.
As much as we hate to admit it, the first thing that many people still think of when they hear the term “tech support” is the experience that comes with an antiquated approach to technology services: the break/fix method. Fortunately for us, we are seeing many businesses make the better decision, and turn to the clearly superior option, managed IT.
When you mention the term 'disaster recovery,' most people think about the big ground-shattering events like earthquakes, fires, floods, tropical storms, etc. While these natural events are certainly disasters and devastating in their own right, smaller things can constitute as a disaster for your business, and they aren't seasonal.