How much control do you really have over your IT assets? Oftentimes, businesses will consider other priorities, like sales, operations, and customer service, before they focus on IT systems and resources. The problem with this is that it creates a significant burden for your business, both in terms of the hidden financial drains and serious security vulnerabilities that undermine your business’ stability.
GTIN Managed IT Blog
Does this sound familiar? Your business is growing, but you haven’t changed your server hardware since you began operations. It’s hindering growth at this point, and you don’t know what to do. The best solution out there is to turn to the cloud. With the right implementation of a cloud-first model, you can effectively future-proof your business so it can grow unhindered.
Cybersecurity is important. Scroll through a few pages of our blog and you’ll see article after article talking about threats and ways to make yourself and your business less vulnerable to cyberthreats. As an IT professional, however, I’d be so much happier if the state of the world didn’t require such a massive effort just to protect oneself and we could just talk about cool stuff you can do with modern technology all the time!
But alas, strong cybersecurity is crucial to virtually any organization, and it’s becoming even more important by the month.
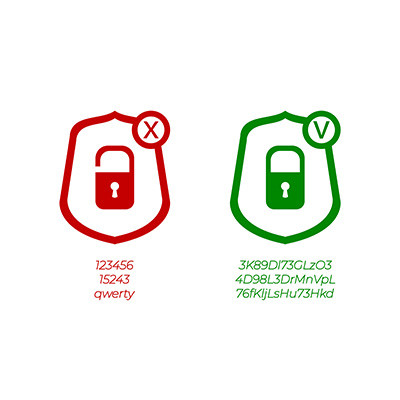
Simple passwords are just not an effective security practice, so if you’re still using credentials like Password, 123456, Guest, or Qwerty, listen up. You need better password hygiene practices before you suffer from a data breach. Here are some ways you can make a better password to protect your business from threats.
Small businesses have a lot to worry about in terms of technology, but one of the things that often gets overlooked is network security. Some small businesses feel that they are too small to be considered a viable target for hackers, but they are wrong; all businesses have data valuable for hackers in some form.
Most organizations are trying to figure out how to secure their IT against the constant flood of threats out there. Unfortunately, the biggest threat out there isn’t something that you can actively protect against. Can you guess what it is?
Unfortunately, it’s your employees, and their potentially lax password practices—and while you can’t really protect yourself against insecure passwords, you can minimize the likelihood that they’ll be used.
Remote work has seen unprecedented adoption in the past few years. While we’re all for the benefits that this trend brings, it is critical that any business that embraces remote or hybrid work does so securely.
Let’s discuss a few measures that your business can and should implement to achieve this security.
Phishing is a remarkably dangerous tactic used by hackers to take advantage of those who might not be quite as in-the-know about security practices. Phishing attacks can be carried out against both businesses and individuals alike, and due to the many different forms these attacks can take—including email, text message, and even fraudulent websites—they can be quite problematic.
Phishing is a common issue that businesses of all kinds can experience, whether they are a small startup or a large corporation. Hackers are always trying to extol information from your employees, including account credentials, remote access to your systems, and in some cases, funds directly from a bank account. It’s up to you to teach them how to identify and respond to phishing attacks.
When I was a kid, there was a Tex Avery cartoon where Droopy Dog was chasing down a crook who escaped from jail. There was a particular scene where the crook (I think it was a wolf in a black-and-white striped jumpsuit) takes a bus, a plane, a ship, and a taxi to a secluded cabin, and then closes a series of increasingly complex doors with a large number of locks, in order to hide away from the pursuing cartoon basset hound.
Of course, when he turns around, exhausted by all the effort he puts in, he realizes that Droopy is standing right behind him, and greets him with a monotone “hello.”
I haven’t seen this cartoon since I was 7 years old, but I almost always think about it when I am using multi-factor authentication.
There is a lot made about ransomware, for good reason. It is quite simply one of the nastiest cyberattacks out there and it demands your attention. A lot of people understand what exactly ransomware sets out to do, but they don’t understand how it got that far and how to address the situation if they have the misfortune of being put in that position.
Your business’ computing infrastructure is a pretty resilient system. It has all types of tools added on to keep malicious code, bad actors, and even sabotage from ruining the good thing you have. This reliability has led to hackers changing the way that they go about their business. Nowadays, most of the attacks that affect businesses are phishing attacks. In today’s blog we will go through the elements of a phishing attack and how you can protect your business from them.
Password changes, multi-factor authentication, and countless changes in policy and procedure can make daily workflows more and more complicated. Cybersecurity can truly be a pain—a necessary pain, granted—but a pain nevertheless, and one that can gradually lead to burnout if you aren’t careful. Let’s go over how to mitigate the likelihood of it.
Do you have an old Google account that you created years ago, only to replace it later with one that is more on-brand and less filled with spam messages? You’re not alone, but as you might expect, these accounts can create more problems than they are worth if you let them sit around unused for too long. Perhaps that is why Google is planning to shut down any old Google accounts that have remained dormant for the past two years.
Ransomware is one of the more dangerous threats out there for businesses of all industries and sizes. To help emphasize just how dangerous it is, however, you have to look past the initial threat of having to pay a ransom and look at the other risks associated with it. We’re here to try to get the point across that ransomware is something your business should absolutely be taking seriously.
In today’s business, sharing files is easy and something many workers take for granted. Unfortunately, not all file-sharing methods are secure. When efficiency is prioritized over security, it can often lead to extremely troublesome situations. For this week’s tip, we thought we’d go through a half dozen practices you can take to ensure your files get to where you need them to get safely and securely.
It’s easy to use the terms “patches” and “updates” as if they mean the same thing, and they are often used interchangeably within the same context. However, understanding the difference between the two can make a world of difference in terms of how you approach implementing each of them. We’re here to clear things up a bit and help you better understand the patches and updates you deploy on a month-to-month basis.
How often do you get emails from individuals claiming to be working with a business who wants to do business with yours or sell you a product, completely unsolicited and even perhaps a bit suspicious? These types of messages can often land small businesses in hot water, as it only takes one phishing email landing in the wrong inbox at the wrong time to put your business in jeopardy.
With cybersecurity a priority for every business that depends on their IT, there are a lot of different strategies being utilized out there to keep threats off of networks and data safe. One of the most advanced strategies being used today is enlisting a service that runs a Security Operations Center (SOC). Today, we’ll investigate what a SOC is and how it works to keep threats at bay.